Outside my day-to-day work for Virus Bulletin, I like to travel the world to attend and, where possible, speak at security events. This year, I have given talks on four different continents, with the fourth one last week at AfricaHackon in Nairobi, Kenya.
Not only was the event great in terms of the organisation and the speakers, but it was also a reminder that security is a global phenomenon that manifests itself in different ways in different countries and regions. I
urge security companies and practitioners to consider attending and supporting security events around the world, to share and to learn.
And though I am sure there is still a lot for me to learn, I am excited that this year’s
Virus Bulletin conference once again features speakers from all continents but Antarctica. The
call for last-minute papers for VB2019 remains open until the end of next week, so please submit your threat analyses and other research, regardless of what part of the world they refer to!
Martijn Grooten
Editor, Virus Bulletin
For the privacy conscious among you: we do not track clicks on the links contained in this newsletter to individual subscribers, but should you feel more comfortable, we believe that any of the links mentioned here can be found through search engines.
Cloud Atlas is a threat actor engaged in cyber espionage whose activities date back to the beginning of the decade. Last autumn, Palo Alto Networks, which calls this group ‘Infection’,
wrote about the
PowerShower backdoor used by this group. Now, researchers at Kaspersky
have noted a change in which PowerShower doesn’t serve as a validator but is downloaded by a new, polymorphic backdoor that the researchers have dubbed ‘
VBShower’.
Last week, Microsoft issued its monthly
software patches in what is still commonly referred to as ‘
Patch Tuesday’. It issued a
specific alert about CVE-2019-1181 and 1182, remote code execution vulnerabilities in Remote Desktop Services. Like ‘BlueKeep’, these vulnerabilities are wormable (and are thus referred to as ‘
DejaBlue’) and though a worm for BlueKeep has yet to appear, the general consensus among the security community appears to be that
DejaBlue is more easy to exploit, making patching a must. A good
overview of all patched vulnerabilities was, as usual, published by the SANS Internet Storm Center.
As usual,
Adobe joined Microsoft in issuing security patches. No patches for Flash Player were released, but patches for
Acrobat and Reader as well as for
Photoshop were made available. Several of the latter vulnerabilities were
found by Fortinet researcher Kushal Arvind Shah.
For a malware author, the advantage of writing in the Go language is that it makes it easy to port malware to different platforms. A good example is
GoBrut, multi-platform malware previously analysed by
Fortinet,
Alert Logic and, under the name
Stealthworker, by
Malwarebytes. Now, researchers at Yoroi have
found an update to the malware which sees the addition of various modules that make it even more effective at brute-forcing various kinds of logins, in particular those related to e-commerce websites.
ESET’s Zuzana Hromcová has
analysed a financially motivated malicious email campaign targeting organisations in Serbia and other former Yugoslav countries. The emails contained a link to a self-extracting RAR archive that showed a decoy PDF file while downloading malware in the background. The downloaded malware was a backdoor named ‘
BalkanDoor’ or a RAT named ‘
BalkanRAT’, with telemetry showing that many victims had both kinds of malware on their machines.
Researchers at ThreatFabric have
analysed Cerberus, Android malware available for rent on underground forums. The malware has various information-stealing capabilities with a specific focus on banking activity and uses Android’s pedometer to evade analysis.
The rather popular
HawkEye keylogger continues to evolve. Cyberbit’s Hod Gavriel has
analysed a new version of the malware that has started using the RegisterRawInputDevices Windows API, a technique previously seen in Metasploit.
Agari’s Crane Hassold has
described how
BEC scammers, and in particular the
Curious Orca group operating out of Nigeria, use blank emails with a single-letter subject to validate the email addresses of potential targets of their operations.
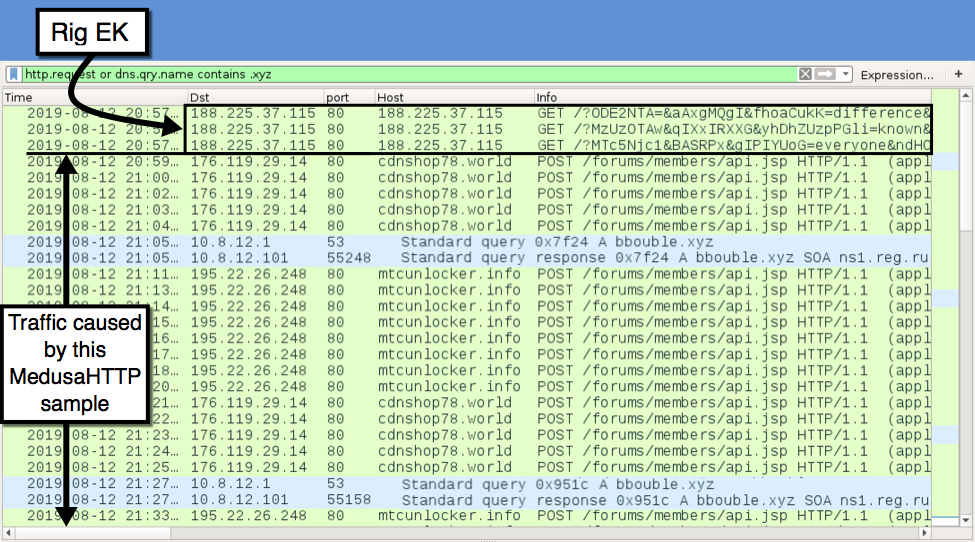
On the SANS Internet Storm Center blog, Brad Duncan has
analysed a recent sample of
MedusaHTTP, that was served by the Rig exploit kit. This malware, used to make infected machines part of a DDoS botnet, was previously
analysed by Netscout (then Arbor Networks) in 2017.
Discovered more than five years ago, the
Gootkit banking trojan is still active and continues to be updated. SentinelOne’s Daniel Bunce has
analysed the first stage of a recent Gootkit sample, including the unpacker and downloader, and the various anti-analysis functions deployed.
The
PsiXBot keylogging and infostealing malware was
first analysed this spring by Fox-IT and has since evolved. In a
new analysis, researchers at Proofpoint note how the malware continues to use the ICANN-independent .bit TLD for C&C communication, but now utilizes the tiny.cc URL-shortening service to obtain the C&C URLs.
Compromised websites play a crucial role in the delivery of many malware families. Sucuri’s Luke Leal
describes how compromised websites were used to serve the
Troldesh (a.k.a. Shade) ransomware.
Trend Micro researchers Augusto Remillano II and Jakub Urbanec have
discovered three botnet campaigns that infected routers in order to use them to perform DDoS attacks:
Neko,
Asher (a variant of Mirai) and
Ayedz (a variant of Bashlite).
In a two-part blog post on the SANS Internet Storm Center blog (
1,
2), Didier Stevens looks at the ISO-like
DAA file format, which was used to deliver malware. Interestingly, and thankfully, unlike ISO files DAAs don’t files open automatically on a standard Windows system.
Trend Micro‘s Aliakbar Zahravi has
analysed a recent variant of
Remcos RAT, a popular piece of crimeware, which arrived via a malicious email campaign and used an AutoIt wrapper for evasion and anti-analysis purposes.
Carbon Black has published a
report on
Smominru,
cryptocurrency mining malware that has been active since the second half of 2017 and which has evolved a lot since then - for example, now joining the trend of using LOLbins. The report also notes a possible link to the
MyKings botnet.
The increase in value of cryptocurrencies is likely behind a recent spike in cryptominers. Varonis has
analysed ‘
Norman’, an XMRig-based Monero miner which uses various layers of obfuscation and which relies on the DuckDNS dynamic DNS service for C&C communication and the downloading of updates.
According to Fortinet’s Jasper Manuel, users in India have been targeted with a malicious email campaign using a fake income tax calculator as a lure. Once the macros in the attached Excel file had been enabled, a version of
xRAT, an open source remote access tool, was installed on the user’s computer.
Avanan researcher Yoav Nathaniel has
looked at a phishing campaign targeting Office 365 users where the user is tricked into opening an HTML attachment that uses the meta-tag to redirect them to the actual phishing site, a technique he dubs ‘
MetaMorph’.
Researchers at Netflix have
discovered vulnerabilities in various
HTTP/2 implementations that could result in DDoS attacks and in some instances even a DoS attack performed by a single system.
Cyberscoop
spoke to a number of security researchers about two samples (
1,
2) recently uploaded to VirusTotal by US Cyber Command that are linked to North Korea’s
Lazarus Group.
Finally, given that this newsletter focuses on technical analysis of digital threats, it is worth reading a
blog post by Dragos researcher Joe Slowik (a VB2018
speaker) who points out that, especially in
ICS security, a lot of damage can be done when a relatively low-skill and low-cost cyber attack is combined with information warfare.
© 2019 Virus Bulletin Limited
The Pentagon, Abingdon Science Park, Abingdon, Oxon, OX14 3YP, UK