Last week, I attended SAS 2019 Singapore, an event which Virus Bulletin was proud to partner. I had never attended SAS before, and had initially been a bit sceptical about an event organised by a vendor (Kaspersky Lab), but I found it to be a very well organised conference with a broad-ranging programme, including talks from some of Kaspersky’s traditional competitors.
Apart from many technical talks, several of which were linked to articles mentioned in this newsletter, the event also included some talks on important subjects such as stalkerware (by the EFF’s Eva Galperin); dealing with the media (by veteran journalist Kim Zetter); and reaching out to the security community in less well represented parts of the world (by Comae’s Matt Suiche). I hope that the audience and the wider security community will not forget the subjects discussed.
SAS also has a fairly large overlap in speakers with the Virus Bulletin conference; more than a dozen of the SAS speakers either spoke at VB2018 last year or are scheduled to speak at VB2019 in London this year. If you attended SAS, or watched what was happening from afar, note that the programme for VB2019 has been published and that registration is now open!
Editor, Virus Bulletin
For the privacy conscious among you: we do not track clicks on the links contained in this newsletter to individual subscribers, but should you feel more comfortable, we believe that any of the links mentioned here can be found through search engines. All links have been added to the Wayback Machine.
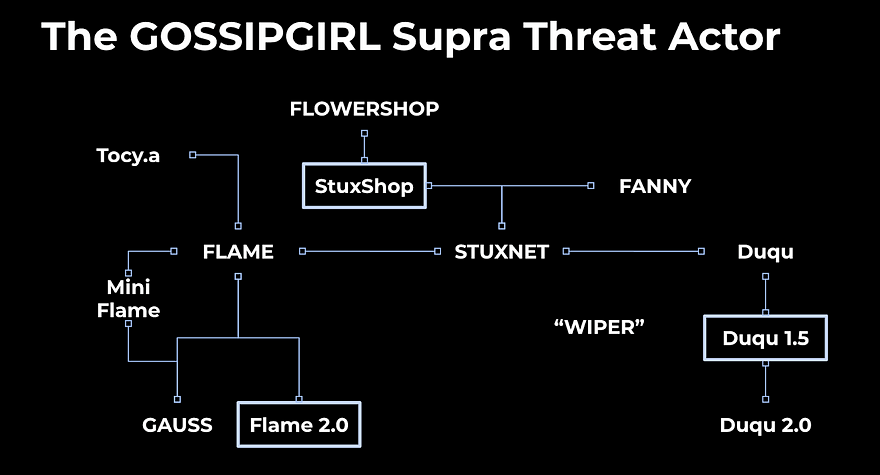
One of the most talked about presentations at SAS came from Chronicle researchers Juan-Andres Guerrero Saade (a regular VB conference speaker) and Silas Cutler. They discussed, both on stage and in a blog post, the Gossip Girl ‘supra threat actor’ whose projects included Stuxnet, Duqu and Flame. They also found evidence of a 2.0 version of Flame, the malware framework that was so spectacularly shut down after its discovery in 2012.
In December 2017, FireEye wrote about TRITON, an attack framework that had been used to target a critical infrastructure facility. The company has now published a blog post on a second attack that uses the same framework to target a different critical infrastructure facility. The detailed blog post shows how the actors used a large number of commodity and custom tools to maintain prolonged and persistent access to the target network. The blog post also rather helpfully includes some tips on how to detect activity from this and related actors. One of the authors of the FireEye research, Daniel Kapellmann Zafra, will speak at VB2019 in London about reconnaissance performed by threat actors against industrial networks.
ESET researcher Romain Dumont has analysed a new macOS backdoor used by the OceanLotus APT group, a previous version of which was analysed by Trend Micro’s Jaromir Horejsi last year. Romain notes some changes compared to the previous version, such as new C&C servers and the use of an external library for network exfiltration, but points out that there is less need to constantly evade detection, given the relatively low prevalence of security software on Macs.
Last autumn, the Emotet trojan started exfiltrating entire emails as opposed to email addresses from infected endpoints. Researchers at Kryptos Logic have now found that these emails are being used by Emotet to ‘inject’ its emails into existing conversations by sending a download link followed by the full previous conversation, exactly as one would expect a reply to look. The emails are sent using legitimate mail servers connected to via stolen SMTP credentials, but the slight silver lining is that the senders are spoofed, which means that SPF and DKIM can still mitigate this threat well.
Emotet isn’t only busy spreading itself. On his Malware Traffic Analysis blog, Brad Duncan writes about how he found it spreading Qakbot, long a common payload spread by Emotet. Sophos researcher Luca Nagy will speak about Emotet at VB2019 in London.
Check Point has analysed a new campaign by the MuddyWater APT group, commonly linked to Iran, that targeted organisations in Turkey. As in previous MuddyWater attempts, the infection starts with a spear-phishing attack against the target, which then ultimately leads to the POWERSTATS PowerShell-based backdoor, first analysed by Palo Alto Networks in 2017. One of the things this backdoor is used for is stealing files that can be used as a lure in further attacks.
Also possibly linked to MuddyWater is a spear-phishing attack analysed by Microsoft that also included a Word attachment with a link, clicking on which would start a complicated attack chain, with the final payload being loaded by exploiting the CVE-2018-20250 vulnerability in WinRAR.
Kaspersky researchers write about Gaza Cybergang, an Arabic-language threat actor predominantly targeting the Palestinian Territories. They have analysed ‘SneakyPastes’, a low-budget operation that forms part of this group, which they say was also behind the Desert Falcons operation and Operation Parliament. SneakyPastes relies on a single C2 server, with most of the payloads being hosted on free ‘paste’ sites like GitHub and Pastebin.
Kaspersky has also published a short overview of TajMahal, a sophisticated APT framework supporting a record number of 80 modules, with a diplomatic entity from a Central Asian country the single known victim.
Following the recent discovery of the Exodus Android spyware by Security Without Borders, Lookout has added its own analysis in which it reports to have found an iOS variant of the same spyware, which has limited functionality compared to the Android version.
Cisco Talos researcher Vitor Ventura has analysed Gustuff, an Android banking trojan that has been targeting Australia, that had previously been analysed by Group-IB. The malware harvests credentials and uses techniques previously seen in mobile malware, such as the use of overlaying webviews or the abuse of the accessibility API. Vitor believes the malware is linked to the ‘ChristinaMorrow’ SMS spam campaign, that also targeted Australia.

Malwarebytes researchers have looked at Baldr, an information-stealing trojan that has been sold in underground forums since the beginning of this year and which was spotted by Microsoft in the wild in February. Apart from a technical analysis of this obfuscated malware, they also looked at its short development cycle and how it has been advertised and sold on underground forums.
Ruchna Nigam, of Palo Alto’s Unit 42 team, has discovered a variant of the Mirai botnet compiled for new processors. Given the availability of Mirai’s source code since 2016, this isn’t too surprising a discovery, yet she also found some minor feature changes in this new variant.
As always, the second Tuesday of the month meant Microsoft released various patches, with two of the related vulnerabilities (CVE-2019-0859 and CVE-2019-0803) already having been exploited in the wild. As always, the SANS Internet Storm Center has a good overview on its blog.
Trend Micro writes about two vulnerabilities in macOS that were patched by Apple last week; both could lead to privilege escalation or denial of service.
Netsparker has analysed a subtle XSS vulnerability in WordPress versions prior to 5.11 that would require an attacker to get a user with administrative privileges to visit a specifically crafted page for arbitrary JavaScript code to be executed, which could be used to execute remote code.
Threatstop has published a timeline of the various malspam campaigns that have been spreading the Lokibot trojan in 2019.
Tenable’s Satnam Narang has analysed CVE-2019-0211, a privilege escalation vulnerability in the popular Apache web server, which is a particular concern on shared hosting environments.
The use of steganography, and in particular the hiding of malicious code inside images, is becoming increasingly prevalent, both in targeted and opportunistic attacks. Carbon Black’s Sam Yoon has written about its (long) history.
Though the Upatre malware downloader hasn’t been very prevalent in the last few years, it remains a viable threat. Cylance has published an analysis of both the protector and the final payload.
Researchers at Yoroi have analysed a malicious Office document referencing elections in Ukraine. The malware uses some interesting if not new techniques to evade detection and in their analysis the researchers explain why they aren’t sure whether it can be attributed to APT28/Fancy Bear.
When a vulnerability in a WordPress plug-in is discovered, the WordPress team closes the plug-in, which prevents new downloads until the issue has been fixed. However, as Sucuri’s John Castro points out using the yuzo-related-post plug-in as an example, this sensible measure also alerts malicious actors to vulnerable plug-ins, which can lead to exploitation of active and yet unpatched installations. The very same is true for another plug-in, Yellow Pencil Visual Theme Customizer, which Wordfence writes about.
In a seasonal blog post, ZScaler’s Krishna Kona looks at various tax-related phishing and malware campaigns, while RiskIQ has published a full report on tax season threats.
Seqrite’s Ghanshyam More has analysed the JCry ransomware, spreading through a fake Flash Player update displayed on compromised websites and notable for being written in Golang.
Another example of ransomware written in Golang is ‘shifr’, which was analysed by Flashpoint researcher Vitali Kremez on his personal blog.
Fortinet researcher Raul Alvarez has analysed the Anatova ransomware, which has been active since the beginning of the year when it was found by McAfee.
Yoroi researchers have analysed an infection that started with a malicious LNK file (a technique used by both cybercriminals and APT actors) and which ultimately led to the installation of LimeRAT, one of many remote access trojans for which the source code is freely available on GitHub.
Trend Micro researchers write about a malicious cryptominer that was first analysed by 360 earlier this year and that is now spreading beyond China. Apart from weak passwords, which it used initially, the malware now also uses the ETERNALBLUE exploit to spread further.
The use of SIM swap fraud to steal large amounts of Bitcoin from Americans has been well documented, but the issue is widespread around the world. Kaspersky researcher Fabio Assolini (a multiple-time VB conference speaker) and André Tenreiro of CERT-MZ write how the technique is widespread in both Brazil and Mozambique.
Directly malicious PDF files have become relatively rare, but a remote code execution in Adobe Acrobat Reader found by Cisco Talos’s Aleksandar Nikolic reminds us that this threat may not have disappeared altogether. A patch for this vulnerability (CVE-2019-7125) has been released by Adobe.
Symantec researcher Candid Wueest has looked at data leakage from hospitality websites through unique confirmation URLs that can be read by third-party sites, such as advertisers, and that in some cases are sent over unencrypted HTTP.
As Norsk Hydro released a video of how its employees kept the company running following a damaging attack by the LockerGoga ransomware, Fortinet researchers Jasper Manuel and Joie Salvio have written another analysis of the malware, which has affected a number of other companies.
Researchers at Imperva have written about how the HTML5 ping feature is used to make users of QQBrowser, a mobile browser especially popular in China, participate unwittingly in DDoS attacks.
Sucuri’s Northon Torga explains how DDoS attacks are performed against the search function on websites running WordPress and what site administrators can do to stop this threat.
At the SANS Internet Storm Center blog, Guy Bruneau has written about phishing emails targeting Office 365 customers.
Cisco Talos researchers Jaeson Schultz and Nick Biasini have looked at how sextortion spam emails have started using embedded images rather than text, and how this is not giving the spammers much success when it comes to delivery rates.
Google has explained how Gmail is to follow the MTA-STS standard, which should mean that emails sent between Gmail and other domains following the standard can’t suffer from man-in-the-middle attacks, which is especially relevant given that a DNS hijack could lead to the theft of emails. SANS Dean of Research Johannes Ullrich has written a blog post on how to implement the standard.
Finally, last week two of the three alleged core members of the Bayrob gang were found guilty by a US federal jury, with the third member having already pleaded guilty in November. At ZDNet, Catalin Cimpanu wrote a very long article on the rise and fall of this Romanian gang, who started out as eBay scammers but ended up running a large and fairly advanced malware operation with very good (if ultimately not perfect) OpSec that helped them remain undetected until their arrest in 2016.
© 2019 Virus Bulletin Limited
The Pentagon, Abingdon Science Park, Abingdon, Oxon, OX14 3YP, UK