“Stop Ignoring Those ‘Update Your Device’ Messages”, Matt Blaze wrote in the New York Times this week. The advice is timely, for the ShadowHammer supply-chain attack might have made people doubtful as to the security of automatically or manually installing software updates. Sure, ShadowHammer wasn’t the first of its kind, nor will it be the last. But on balance such attacks are rare, and more often than not pulled off by very skilled actors. If these are in your threat model you need to seriously change your online behaviour in a way that goes far beyond disabling updates. Nevertheless, supply chain attacks are very real and pose a serious challenge to the security industry. An average user shouldn’t be overly worried about them, but the security industry should take them extremely seriously.
Editor, Virus Bulletin
For the privacy conscious among you: we do not track clicks on the links contained in this newsletter to individual subscribers, but should you feel more comfortable, we believe that any of the links mentioned here can be found through search engines. All links have been added to the Wayback Machine.
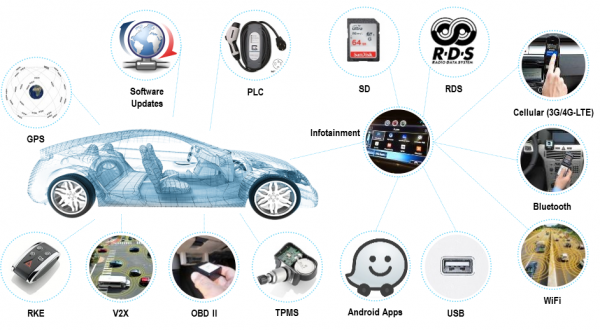
The hacking of a Tesla Model 3 at the most recent Pwn2Own competition was a highlight of the event and a sign that car hacking has become something car manufacturers are taking seriously. A good introduction to the subject of car hacking was presented by Argus Cyber Security's Inbar Raz at VB2018 in Montreal last year. Last week, we published both Inbar’s paper and a video of his presentation.

At Motherboard, Kim Zetter reports on ShadowHammer, a supply-chain attack that led to a malicious update being served to about half a million ASUS PCs. However, only on some 600 devices (based on their MAC address) would a second-stage payload have been downloaded. This, combined with the fact that the malware was delivered from and digitally signed by ASUS, helped keep it under the radar. Kaspersky Lab, which discovered the attack, has some limited technical details, with more being revealed at the company's upcoming SAS conference (of which Virus Bulletin is a partner), while Countercept and Morphisec have both published analyses of the malware. Kaspersky says it believes the group behind the backdoor is the same as that behind the Winnti backdoor which, according to ESET, is still active.
Security Without Borders has published a piece about Exodus, Android spyware made by an Italian company (eSurv) and targeting Italians. Instances of the malware were found in the Google Play Store, disguised as mobile operators’ service applications. Though the malware checks the phone number and its IMEI, a second-stage payload is downloaded regardless of the outcome of the checks. A non-technical write-up, including some legal implications, has been put together by Lorenzo Franceschi-Biccherai at Motherboard.
Symantec has looked at the Elfin espionage group (also known as APT33 and linked to Iran by other researchers), which has been attacking organisations around the world though predominantly in Saudi Arabia and the United States. Recently, the group has been using the same WinRAR vulnerability (CVE-2018-20250) as is being used in many opportunistic malware attacks. In December, an organisation was attacked by Elfin and Shamoon at around the same time, which led to speculation that there may be some link between these groups.
Elfin isn’t alone in using that WinRAR vulnerability: FireEye looked at various other cases in which the vulnerability is being used in targeted attacks.
NetScout’s ASERT team has analysed a new threat actor it calls ‘LUCKY ELEPHANT’, which engages in spear phishing campaigns targeting government, military and telecommunication operations in South Asia outside of India - which probably explains why the researchers are moderately confident that this APT actor is operating from India.
The Scanbox reconnaissance framework was first analysed by AlienVault in 2014 and has been used in various watering hole attacks by different China-linked APT groups since. Now, Recorded Future has written about how the framework was found being used on websites belonging to the Pakistani government and the Central Tibetan Administration.
Kaspersky researchers have analysed an ongoing campaign by North Korea’s Lazarus Group targeting cryptocurrency exchanges using custom PowerShell scripts and two pairs of C&C servers: registered ones to host malware and compromised ones for communication.
The PsiXBot information-stealing malware has been around since at least 2017 but did not become widespread until recently, when it was served by the Spelevo exploit kit and pushed by the Smokeloader malware downloader. Fox-IT researchers Stefano Antenucci and Antonio Parata have analysed the malware, its recent changes, and the various modules that are part of it.
In a watering hole attack, a site likely visited by a select group of targets is compromised, often to serve tailored malware. Trend Micro has discovered a slight variant of such a campaign in South Korea (which it names ‘Soula’), where at least four prominent websites were compromised to serve, via JavaScript, a phishing form that was tailored to the kind of device the visitor was using.

ZScaler researcher Mohd Sadique has looked at compromised Joomla and WordPress sites serving malware (the Shade/Troldesh ransomware) from the /.well-known/ directory. This directory is commonly used to prove ownership of a domain, for example by Let’s Encrypt; hence the compromised sites were all using HTTPS.
Kaspersky researchers have written about Brazilian malware using the old trick of prepending malicious ZIP files with three bytes representing the Byte Order Mark (BOM) usually found within UTF-8 text files. This means some scanners will fail to recognize the file as a ZIP archive, yet many utilities will still unpack the files.
Writing YARA rules is an important part of many a malware researcher’s job. It tends to involve a lot of manual work, as raw executable code needs to have its variable values replaced by wildcards before it can be copied. Researchers at Fox-IT have now released a tool, mkYARA, that automates this process; it has been made available on GitHub.
The Emotet downloader plays a crucial role in many cybercrime campaigns. Researchers from Trend Micro have analysed a campaign in which Emotet downloaded the Nymaim malware, which then pushed the Nozelesn ransomware, which has targeted Poland in the past. Nymaim has been around for some years and was the subject of a VB2016 presentation by researchers from CERT Poland.
Researchers at Spamhaus have looked at changes made in the HTTP requests made by Emotet and found them hard to distinguish from legitimate HTTP traffic.
Another prevalent threat is Ursnif. Yoroi researchers have looked at a recent campaign targeting Italy that started with a VBScript hidden inside an archive attached to an email.
SentinelOne has looked at yet another prevalent piece of malware, the Trickbot banking trojan, by analysing a recently caught sample.
Malwarebytes has looked at the BatMobi Android adware that injects (harmful) ads whenever the user visits Google Play.
Password-protected Office documents remain an effective way to evade anti-malware scanners in email security products, even if the password is something trivial. Brad Duncan has looked at some recent examples serving the Dridex malware.
As the LockerGoga ransomware continues to disrupt operations at a few targeted victim organisations, both F-Secure and Palo Alto Networks have published analyses of the malware.

Security researcher ‘Fumik0_’ has written a very detailed analysis of Qulab, an information stealer written entirely in AutoIT, and which applies a time-consuming, if not too complicated obfuscation method.
Malwarebytes researcher Jérôme Segura has looked at how vulnerable plug-ins in open source CMSs such as WordPress are being used to redirect traffic to scams and exploits.
One of those vulnerabilities was one recently found in the Social Warfare plug-in for WordPress. Wordfence’s Mikey Veenstra explains that this was a remote code execution rather than a less serious XSS vulnerability.
Confiant has published a piece describing how multiple layers of cloaking have been employed in ad fraud campaigns by what it calls the Dandelion Group.
Yoroi has analysed a new variant of Qrypter, malware-as-a-service that is often used in combination with Adwind/jRAT, a previous version of which was analysed by Trustwave last year.
In the meantime, a new stored XSS vulnerability in WordPress itself has been found and patched, which Sucuri wrote about. Such vulnerabilities require human interaction to exploit, but do make any unpatched WordPress site vulnerable.
Certainly important to fix is an SQL injection vulnerability in both the open source and commercial versions of Magento. RiskIQ's Yonathan Klijnsma, who has reported widely on the Magecart groups that have exploited these vulnerabilities to install web skimmers, has already reported a significant rise in web skimming injections as a consequence.
On the SANS Internet Storm Center blog, Xavier Mertens has written about creating your own Passive DNS service, a subject which was also covered by researchers from Plunk at VB2016 in Denver.
Cyren has looked at various examples of Apple phishing emails.
Cylance has analysed Njw0rm, a RAT with worm-like capabilities, by looking at both the builder and the malware itself.
SentinelOne’s Philip Stokes has written an introduction to how malicious PDFs can execute code.
Emsisoft has released a decryptor for the HKCrypt (or Hacker) ransomware.
Finally, Palo Alto Networks’ Brad Duncan explains how to identify hosts and users from network traffic displayed in Wireshark, which can be very helpful when analysing malicious traffic on a network.
© 2019 Virus Bulletin Limited
The Pentagon, Abingdon Science Park, Abingdon, Oxon, OX14 3YP, UK