Welcome to the latest edition of the Virus Bulletin newsletter, in which we serve the threat intelligentsia with interesting analyses from around the web. Old editions of the newsletter can be found
on our website, where you - and your colleagues - can also
sign up to receive these newsletters directly in your inbox. And please don’t hesitate to send us your comments and suggestions; these newsletters are compiled by VB Editor Martijn Grooten (
[email protected]).
For the privacy conscious among you: we do not track clicks on the links contained in this newsletter to individual subscribers, but should you feel more comfortable, we believe that any of the links mentioned here can be found through search engines. All links have been added to the Wayback Machine.
We are excited to announce that later this week we will open the Call for Papers for
VB2019, the 29th Virus Bulletin Conference, which is to take place in London, UK, 2-4 October. The deadline for submissions will be 17 March, so you’ve got a little over two months to send a proposal. We strive to make VB2019 the best and most international threat intelligence conference, and we can only achieve that by having submissions from as broad a section of the community as possible.
Of course, there are
other ways to contribute; don’t hesitate to ask about sponsorship opportunities or other ways to contribute to the event!
To put you in the mood for the CFP, we have uploaded a
VB2018 paper by Google researcher Maddie Stone in which she reverse-engineered an anti-analysis library used in many malicious Android apps. Owing to its many layers, Maddie dubbed the library ‘WeddingCake’. We have also uploaded the
video of Maddie's VB2018 presentation.
Maddie’s colleague Lukasz Siewierski also spoke at VB2018; we have already published
the video of his talk on Triada. For Google’s Security blog, Lukasz recently
analysed another family of potentially harmful applications, dubbed ‘Zen’, which he found to exhibit a wide range of techniques, from inserting an advertising SDK to the use of an advanced trojan.
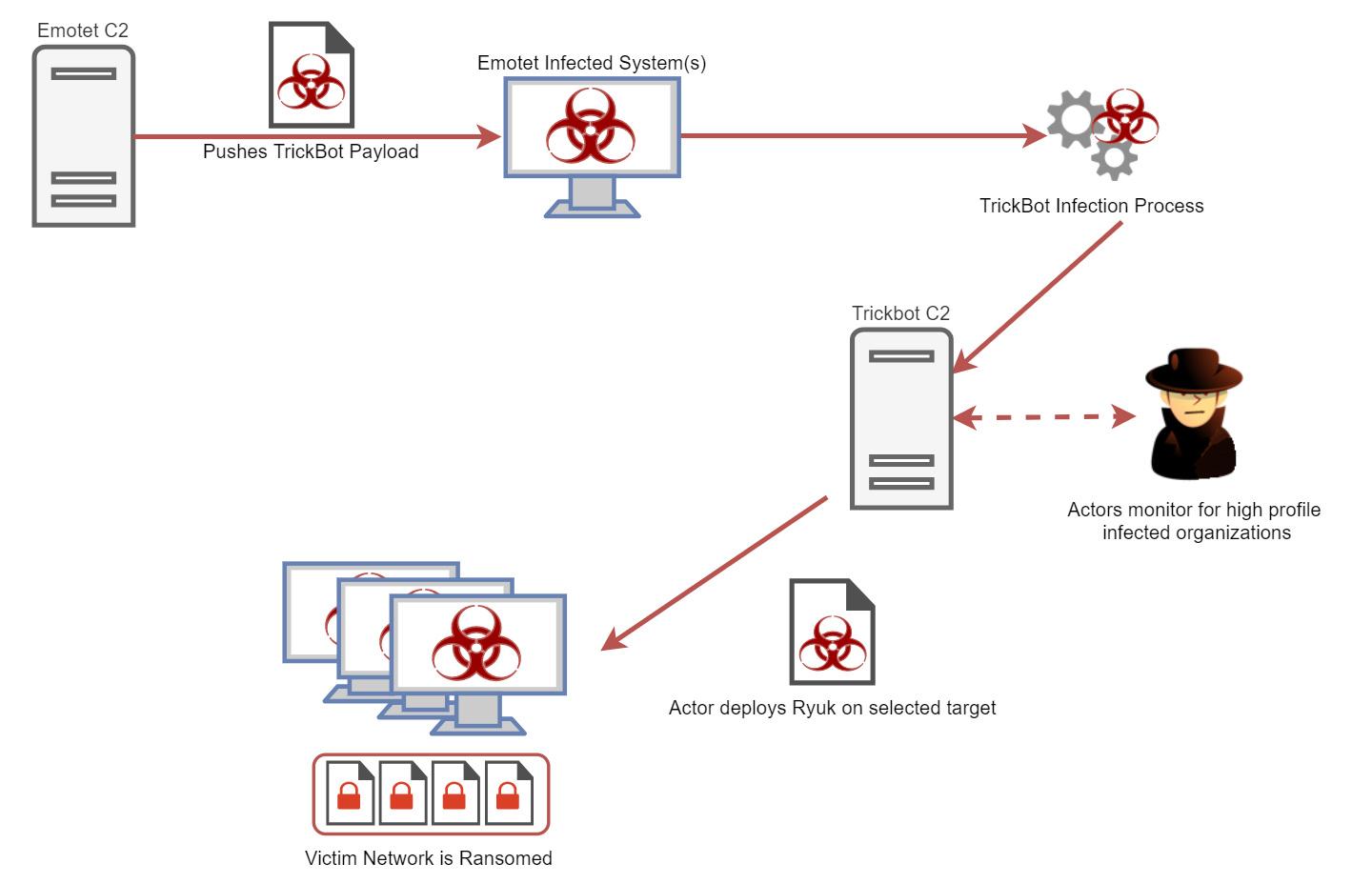
Some prominent attacks put the Ryuk ransomware firmly in the spotlight late in 2018. The use of its predecessor, Hermes, by the Lazarus Group had led some to suggest that North Korea had a hand in these attacks, but most security researchers were sceptical about these claims.
No fewer than four new blog posts were published last week that justify this scepticism. McAfee
links both Hermes and Ryuk to actors in the Russian-speaking cybercriminal underground, while Kryptos Logic
explains how the infections likely started with the Emotet trojan, which in turn downloaded Trickbot, through which Ryuk was pushed onto selected targets. The delivery of Ryuk via Trickbot was also
analysed by FireEye. Finally, Crowdstrike
confirms what BAE Systems had previously
suggested- namely that the use of Hermes by the Lazarus Group in 2017 was merely by way of a cover-up: its analysis explains how the ransomware as it was deployed in that attack would not have allowed for decryption anyway.
In November last year, Cisco Talos
published research into a threat actor, mostly active in the Middle East, that both attacked and utilized DNS infrastructure and which was thus given the name ‘DNSpionage’. FireEye has now published
more details on how this group hijacked DNS and how this was used in further attacks - for example the creation of rogue TLS certificates. The company also attributes the attacks ‘with moderate confidence’ to Iranian actors. In the meantime, Lastline published its
own research on this actor, which it refers to as ‘Cold River’, while Openminded’s CERT
looked at the actor from a target’s point of view, including how it moved laterally within the organisation.
Attacks by Fancy Bear (a.k.a. Sofacy, APT28 or Sednit) continue to be analysed, which is in part because of “its characteristically higher volume for a targeted attacker” (as Kaspersky researchers describe it). The Kaspersky researchers
analysed a variant of the group’s Zebrocy downloader written in the Go language, which builds upon a previous
analysis of the malware by Palo Alto’s Unit42 group.
The Government of Singapore has published a
long report containing quite a few technical details on the theft of the health data of 1.5 million of the country’s citizens, which it attributes to a nation state. Kaspersky’s Costin Raiu posted a
summary of the report on Twitter.
Despite some recent law enforcement successes against various DDoS actors, this type of threat remains very active. One prominent actor in this space has long been ‘ChinaZ’. In a
blog post published last week, Intezer’s Ignacio Sanmillan links ChinaZ not only to the ‘Billgates’ malware but also to Nitol and, through its use of the Gh0st RAT, even to the Iron Tiger APT group.
One group that is a disproportionately large target of DDoS attacks is that of human rights campaigners. The use of a professional DDoS service, or booter, that used three different relays to target an Israeli human rights website was
analysed by eQualit.ie, who also worked to shut down this operation.
The peer-to-peer nature of the Hide’N’Seek IoT botnet (first discovered by researchers from Bitdefender, who
spoke about it at VB2018) should make it harder for researchers to map the botnet. However, as researcher ‘MalwareTech’
points out, “botnet operators must decide between making peer discovery difficult and having a stable botnet” and thus he was able to crawl the botnet relatively easily.
Researchers at ZScaler have
analysed a sample of the Mjag dropper, written in .NET, which they found to be buggy. However, after they patched the bug, they saw it download the Punisher RAT which, among other things, steals information from the infected device.
Microsoft has published its first
regular patches of 2019. As always, the SANS Internet Storm Center has a
useful overview. Probably most interesting, and most worrying, among the patched vulnerabilities is
CVE-2019-0547, a flaw in the Windows DHCP client, which could be exploited by a malicious DHCP server.
Several less severe vulnerabilities affected the Microsoft Windows JET Engine. One of these was CVE-2019-0538, a code execution vulnerability which was discovered by Fortinet researcher Honggang Ren, who wrote a
detailed blog post about it.
Also from Fortinet comes an
analysis of a cross-site scripting vulnerability in Magento core. Now patched, the vulnerability could have allowed a determined attacker to take over the administrator account of an e-commerce site running Magento.
Trend Micro
has found no fewer than 85 pieces of Android adware on the Google Play store, which were downloaded 9 million times in total.
Spamhaus has an
interesting article on BGP hijacking and how it has long been used by spammers to send their email from supposedly ‘clean’ IP addresses.
Carbon Black
analyses the Djvuu ransomware, which shares similarities with both the Stop ransomware and the Goren-B trojan and which, rather intriguingly, requires a victim to have an account on the Pirate Bay.
Cisco Talos’s Mike Bautista has created a
decryption tool for the PyLocky ransomware (analysed by Trend Micro in September last year), with the important caveat that it requires the original C&C traffic to have been recorded.
Coveware
writes about Cryptomix, a lesser known malware that claims the ransom payment actually goes to a children’s charity.
Last year, Flashpoint researcher Ronnie Tokazowski won M³AAWG’s prestigious
JD Falk Award for his work fighting business email compromise (BEC) fraud. He continues to fight these potentially very damaging threats and has now
set up a TLP:White Slack channel for those active in this space.
Trend Micro has recently written about
ethics and trust in underground forums and how this trust is somewhat broken.
FireEye’s David Via
writes about the various methods available for anyone who, during forensic analysis of a Windows machine, wants to study historical and deleted registry data.
Exploit kits have not been particularly active in the past month - something that is likely related to the holiday period. Various Rig campaigns have continued to be seen though. Brad Duncan
observed Rig’s HookAds campaign spreading the new Vidar malware, after Jerome Segura had previously
been delivered the malware by the Fallout exploit kit.
Brad also
analysed a campaign where compromised websites were pushing a support scam via pop-ups.
Sucuri’s Rianna MacLeod
looked at how a free widget that shows a visitor counter on websites led to some unwanted redirects to a dating site.
As always, the My Online Security blog looked at various spam campaigns:
fake ‘Inquiry’ emails pushing the destructive Renamer malware;
fake purchase orders pushing the Megalodon trojan using subdomains of legitimate domains hosted on GoDaddy;
fake DHL quotations using the rather obscure .ace format to deliver Lokibot;
a campaign delivering HawkEye via new kinds of RTF files, which still exploits CVE-2017-11882; and a
phishing scam targeting CashPlus users.
Avanan’s Yoav Nathaniel
explains how spammers are using zero-width spaces to split URLs and thus bypass filters like that of Office 365.
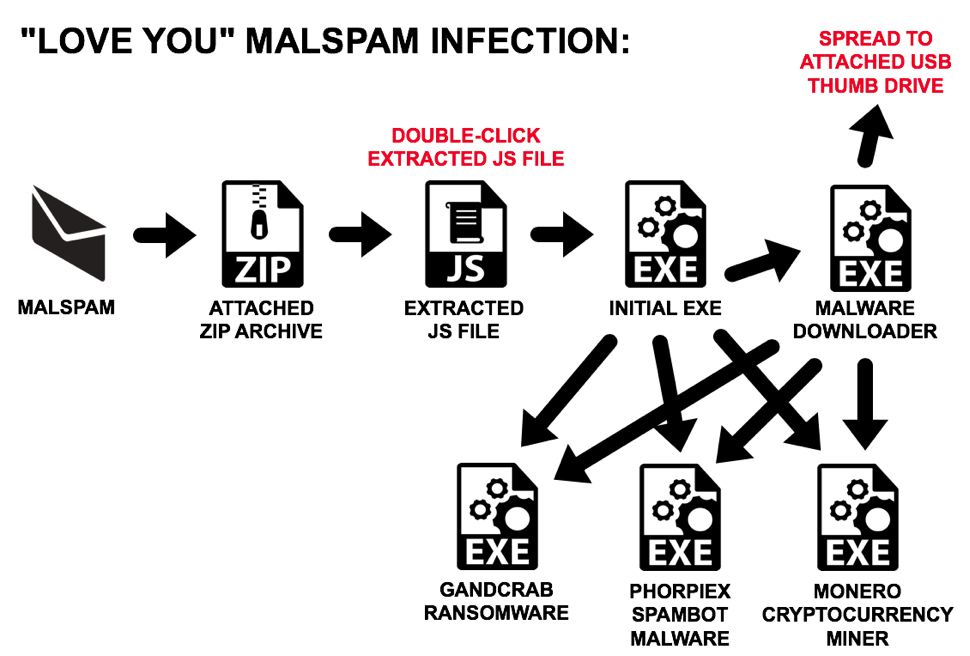
Almost two decades after the infamous ILOVEYOU virus, ‘love’ remains a common lure to spread malware. In a post on the SANS Internet Storm Center blog, Brad Duncan
analysed a fairly large campaign with subjects like ‘I love you’ that used zipped .js attachments to spread various kinds of malware, including the GandCrab ransomware and the Phropiex spambot.
Also at the Internet Storm Center, Didier Stevens
explains how to analyse potentially malicious Office attachments protected with a password, a fairly common trick used by spam to bypass filters.
Sophos’s Paul Ducklin has
looked at some recent SMS phishing examples on the company’s Naked Security blog.
The ubiquity of HTTPS makes it unrealistic for test or development sites not to support it. Filippo Valsorda has written
a tool that solves this problem by creating a (local) root certificate that can be used to create valid certificates for any domain, including localhost.
Given the slow to steady rise of malware targeting macOS, high-risk targets and those working to protect them may want to check out the
detailed hardening guide written by Germany’s ERNW.
Given its continued popularity, hasherezade has
released an updated version (0.3.9) of PE-bear, a flexible “first view” tool for PE files.
Finally, for those who like to listen to threat analyses, there are two interesting podcasts. Forcepoint’s Mike Mimoso
spoke to researcher Allison Nixon on the takedown of various DDoS-for-hire services just before Christmas, while The Cyberwire
spoke to RiskIQ’s Yonathan Klijnsma on the various groups labelled under the ‘Magecart’ umbrella.
© 2018 Virus Bulletin Limited
The Pentagon, Abingdon Science Park, Abingdon, Oxon, OX14 3YP, UK