Welcome to another edition of the Virus Bulletin eNews newsletter! One of the reasons we started this newsletter was to provide you with the best, unbiased overview of threat analyses from around the world, even in the 51 weeks a year in which no Virus Bulletin Conference takes place.
Undoubtedly, many of the authors of the various articles we link to in these newsletters will be at the next Virus Bulletin Conference (
VB2019 London, 2-4 October 2019), whether as speakers, attendees or maybe as sponsors. Last week we published a
blog post about the conference, in which we also asked for suggestions as to how we can improve on the event still further.
We also welcome your comments on and suggestions for this newsletter; please contact VB Editor Martijn Grooten (
[email protected]), who compiles it every week. And don’t hesitate to tell your friends and colleagues to
sign up!
For the privacy conscious among you: we do not track clicks on the links contained in this newsletter to individual subscribers, but should you feel more comfortable, we believe that any of the links mentioned here can be found through search engines. All links have been added to the Wayback Machine.
Fidelis recently published a short paper (
pdf) about the revived Cobalt/Carbanak group using an updated version of the
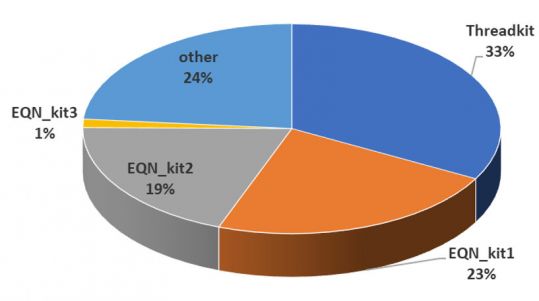
Threadkit exploit builder (also
previously used by the same group) to generate malicious Office files. For us, this was a good reason to
publish the VB2018 conference paper by Sophos researcher Gábor Szappanos, who looked at active exploit builders and in particular the use of
CVE-2017-0199, which was also the vulnerability exploited in the case Fidelis reported on. We also released the
video of Gábor's VB2018 conference presentation.
Last week we also
published the video of the VB2018 presentation by Check Point researcher Aseel Kayal on
APT-C-23, a group that has been active in the Middle East, with a particular focus on the State of Palestine. In her presentation, Aseel not only provided a technical overview of the malware used by this group but also (in true VB conference spirit) connected the various dots between other vendors' reports on this threat actor.
Though Microsoft has stopped referring to it as such, the second Tuesday of the month remains known across the industry as ‘
Patch Tuesday’. As always, SANS ISC provided a useful
overview of the various vulnerabilities patched this month, their severity, and whether they have been exploited in the wild.
This month, only one such vulnerability is believed to have been exploited in the wild prior to a patch being released: CVE-2018-8611, a race condition in the
Kernel Transaction Manager. It was discovered by Kaspersky Lab researchers Boris Larin and Igor Soumenkov, who reported the vulnerability to Microsoft and wrote a
blog post about it. They warn that it is especially dangerous and could be used to escape the sandbox in modern web browsers. Its in-the-wild usage is linked to various APT groups, including
Fruity Armor and the new
SandCat group.
Shamoon is piece of wiper malware that targeted the oil industry, first in
2012 and again in
2016. Last week a new variant was found (uploaded to
VirusTotal) that has been linked to Sapien, an Italian oil services firm.
Symantec and
Palo Alto both analysed the new variant, which the former says has also hit two other organisations in the same industry, based in Saudi Arabia and the United Arab Emirates. At VB2018 in Montreal, Saher Naumaan from BAE Systems Applied Intelligence presented a
paper on
wiper malware, in which the earlier variants of Shamoon featured prominently.
Symantec also posted an
overview of
Seedworm (perhaps better known as
MuddyWater), another cyber espionage group active in the Middle East. Intriguingly, the group’s activities can be linked to both a public GitHub repository and a public Twitter persona - the latter of which follows many of the researchers who have written about this group.
The Virut file infector operates at the other end of the malware spectrum from these attacks. Active since at least 2006, it too appears to have made some kind of comeback, according to an
analysis by Christian J Dietrich.
McAfee has published a
report on what it calls ‘
Operation Sharpshooter’, a targeted attack against nuclear, energy and defence companies that delivers ‘Rising Sun’, an implant used to perform reconnaissance on the target's network. The campaigns share many similarities with previous activity by the
Lazarus Group - similarities that are so obvious that McAfee warns of a possible false flag.
Sofacy, whose various other names include
Fancy Bear and APT28, continues to be very active. Palo Alto has published a
detailed analysis of various recent spear-phishing campaigns conducted by the group, all of which shared the author name ‘Joohn', used current affairs stories as a lure, and delivered the
Zebrocy or
Cannon first-stage payloads.
Cylance has
analysed a long-running malware attack against critical infrastructure in Russia that it believes is criminal rather than geopolitical in nature.
Certfa, which serves as a CERT for the Farsi-speaking community,
reports on a new phishing campaign linked to the
Charming Kitten group that had previously been the subject of a 2017
report by ClearSky. The group targets individuals involved in the sanctions regime against Iran, as well as
Iranian civil society. Certfa points out that the phishing campaign also targets 2FA codes and thus urges high-risk targets to switch to using two factor authentication based on physical security keys rather than relying on 2FA codes. The organisation has posted some
clarifications to its report on Twitter.
ESET researcher Lukas Stefanko recently
found a rather devious
Android trojan that tricks the user into enabling Android
accessibility services, a feature that assists users with disabilities in using Android devices and apps. Once the services have been activated, the malware waits for the user to launch the PayPal app and then uses the previously acquired privileges to steal money - because the user him/herself logs into the
PayPal app, the malware bypasses two-factor authentication. Though this app wasn’t found in the official
Google Play store (which simultaneously made it harder for someone to get infected by it
and harder for the app to be removed) various related apps were available there. These also abuse accessibility services and appear to be targeting users in Brazil. Dr.Web
looked at this latter family of apps, which have since been removed.

Trend Micro researcher Mohamad Mokbel has written a
research paper on an 18-year-old (!) implant found among the
Shadow Brokers leaks (and thus likely attributed to the NSA) that is likely to be part of a larger, yet unknown exploitation framework.
Also from Trend Micro comes an
analysis of an illicit
cryptocurrency miner that exploits three- and four-year-old vulnerabilities in
Elasticsearch. Reminding us of the prevalence of such malware, the miner lists dozens of competing miners that it attempts to remove from the system.
Another Trend Micro
analysis worth reading comes from Muhammad Bohio, who looked at a piece of malware named
Berbomthum that hides its C&C commands in memes posted on Twitter accounts that have specifically been set up for the purpose. The use of social media for malware C&C isn’t new, of course: a
VB2015 paper by F-Secure researcher Artturi Lehtiö provides a good overview of the subject.
And a fourth Trend Micro analysis
looks at ‘
Novidade’, an
exploit kit that targets vulnerable routers by first probing the IP address of the router on the local network and then trying a number of web-based vulnerabilities to compromise it, with the ultimate goal of changing the DNS settings.
Through its own threat intelligence platform, Avast has
found a fake
Netflix Android app that steals
SMS messages.
IoT botnets continue to find exploitable vulnerabilities in order to add more connected devices to their control. Arbor Networks
says it takes only a few minutes before a newly connected device is probed for vulnerabilities.
Malwarebytes researcher Pieter Arntz provides a
short overview of the Eternal* family of
SMB exploits, of which
EternalBlue (found among the Shadow Brokers leaks and used by the WannaCry worm) is the best known, but far from only member.
At the most recent Black Hat Europe conference, Lookout researchers Kristin Del Rosso and Michael Flossman
spoke about the activities of the
Syrian Electronic Army, which mostly concentrate on Syria itself these days. No technical details appear to be available beyond the presentation slides (
pdf), but Thomas Brewster
wrote up a summary for Forbes.
Coveware
writes about how some victims of the
GlobeImposter ransomware are at a loss, as the Tor-hosted site used to handle payments has become inactive. Variants of the ransomware that use email to communicate with the perpetrator still appear to work.
‘
DOSfuscation’ is an obfuscation technique for PowerShell scripts that is commonly used to hide the payload in malicious Word documents. On the SANS ISC blog Didier Stevens
looked at one recent example and, in
another blog post, explained how to deobfuscate such code.
As a downloader,
Nemucod has played a subtle but important role in various malware campaigns, including in the past the delivery of the TeslaCrypt and Locky ransomware. Cylance has published a
technical analysis of the downloader.
In a
two-
part analysis, IBM researchers have looked at malware used by cybercriminals in
Brazil, and in particular the use of the
remote overlay technique.
Even before the GDPR led to the removal of some data from public
WHOIS records, these records excelled in inconsistency. Rapid7’s Kwan Lin
explained how he used
data science to add order to this mess.
Recorded Future has published a detailed
analysis of the often overlooked cybercriminal underground in
Japan.
InfoArmor has published a brief
report outlining the availability online of the taxpayer registry identification numbers of 120 million
Brazilian nationals.
At SANS ISC, Remco Verhoef
warns against malicious
Docker containers and briefly explains how to analyse them.
FireEye has published a deeply technical
blog post explaining how
deep neutral networks (a machine learning method) learn what malware is.
On Thursday, a large
spam campaign informed recipients that an
explosive device was located in their building and that it would go off unless $20k in bitcoin was paid by the end of the day. There was no evidence to suggest that the emails (of which Gary Warner
lists various examples) targeted specific recipients, yet they appear to have led to a number of evacuations. Both
Cisco Talos and
Appriver link the spam campaign to a previous
sextortion campaign.
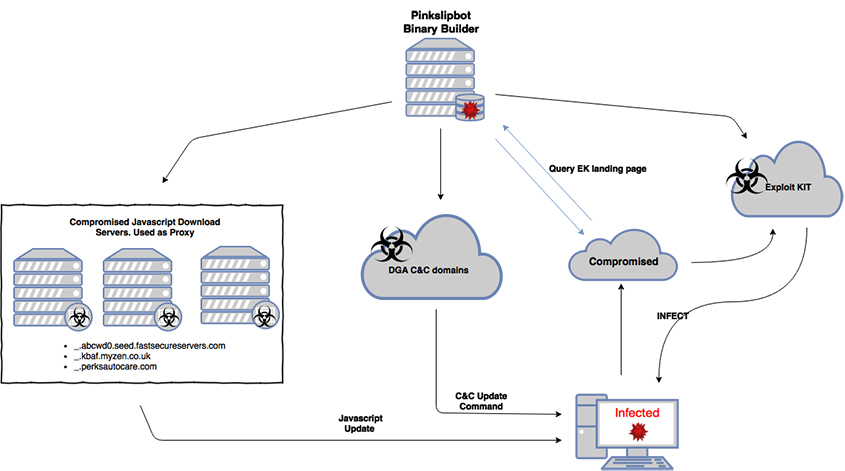
Brad Duncan’s Malware Traffic Analysis blog
reports on an
Emotet malicious spam campaign delivering
Qakbot. Qakbot, also known as Pinkslipbot, is an often overlooked malware family that primarily targets the United States and has many businesses and organisations among its victims. It was the subject of a VB2016
paper by researchers from McAfee.
Qakbot was also listed by Group IB as one of the sources of some 40,000 credentials of
government portals discovered online. The
report is in Russian, but ZDNet has a
summary in English.
Also from Brad Duncan comes a
brief analysis of a malicious spam campaign delivering the lesser known
Imminent Monitor RAT. This RAT was
analysed by Fortinet earlier this year.
My Online Security looked at
two spam campaigns that deliver malware through a redirect hosted on
Google Docs - something that will make both users and spam filters less suspicious of the link.
Other
spam campaigns used failed
email delivery, failed
parcel delivery, and
Brexit as lures, while an
Emotet campaign
delivered IcedID/Botbot, and a campaign of messages containing password-protected Word documents
pushed Nymaim.
Spamhaus
explains why emails sent by Marriott notifying its customers of the
Marriott data breach may have ended up in people’s spam folders.
The Citizen Lab has an
overview of the various litigations and other formal complaints that have been filed against companies selling
digital surveillance software.
Tencent
warns about a serious vulnerability, named ‘Magellan’, in
SQLite. Given how widely this database is used, it should not be ignored.
Vitor Ventura, a Cisco Talos researcher,
shows that the endpoint is the weakest link in secure messaging platforms, looking at side-channel attacks against
WhatsApp,
Telegram and
Signal. These attacks provide lessons for high-value targets who may want to think twice before using the desktop versions of these apps.
In a five-part analysis (
1,
2,
3,
4,
5), Natalie Silvanovich from Google’s Project Zero has shared her efforts fuzzing various
video conferencing applications and her surprise at finding bugs that are both frequent and shallow.
The success of
fuzzing to find vulnerabilities was also shared recently by researchers from Check Point who used WinAFL to
find no fewer than 53 CVEs in
Adobe Reader, at least one of which had previously been used in the wild.
RiskIQ
warns that the still widely used
PHP 5 is about to reach its end-of-life.
Kaspersky Lab has published a
report detailing vulnerabilities in the ChargePoint
chargers for electric vehicles.
A new version of
phpMyAdmin, that fixes various security issues, has been
released.
Detectify
found three serious vulnerabilities in a very popular
JavaScript repository used to allow
file uploads on websites.
Finally, as a follow-up to last week’s ‘
DarkVishnya’ story of
banks being attacked through
hardware devices dropped on the network, Rob Graham
shared how this technique is commonly used by hackers and pen-testers.
© 2018 Virus Bulletin Limited
The Pentagon, Abingdon Science Park, Abingdon, Oxon, OX14 3YP, UK