Welcome to another edition of the Virus Bulletin eNews newsletter, which features all the details behind the security news - the newsletter that focuses on the technical analyses and tools that are essential reads for anyone generating and/or consuming threat intelligence.
We would really like to hear what you think of these emails. The newsletter is compiled by Virus Bulletin Editor
Martijn Grooten (
[email protected]), who welcomes your tips and suggestions. And if you haven’t already done so, don’t forget to
sign up!
For the privacy conscious among you: we do not track clicks on the links contained in this newsletter to individual subscribers, but should you feel more comfortable, we believe that you can find any of the links mentioned here through search engines. All links have been added to the Wayback Machine.
The
indictment, unsealed last week by the US Department of Justice, of two Iranians alleged to have been behind the
SamSam ransomware is a strong reminder that our fight against online malicious activity isn’t pointless and that even those threat actors that perform strong OPSEC have a hard time remaining hidden.
The best technical resource on SamSam is a research
paper published by Sophos earlier this year. The paper was also the basis of a VB2018 presentation by Sophos researcher Andrew Brandt, the recording of which we
released this week.
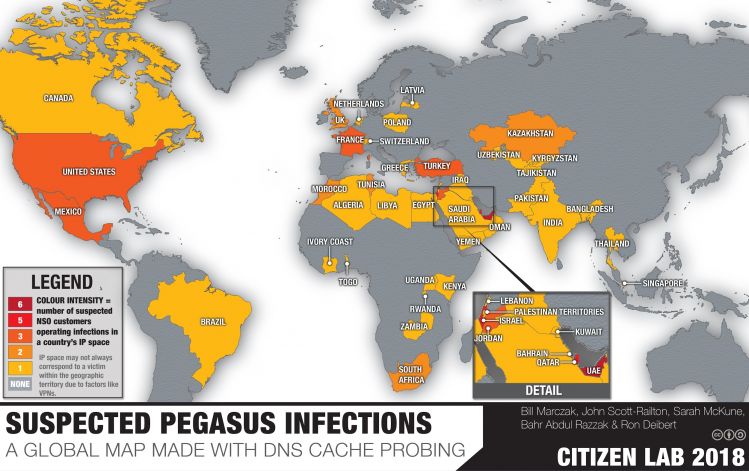
A
new report from the Citizen Lab on the targeting of
Pegasus spyware against colleagues of a murdered Mexican journalist is a sad reminder that the malware's technical capabilities aren’t what should concern us most about this iOS spyware and its developer NSO Group.
Citizen Lab researchers John Scott-Railton and Masashi Nishihata spoke at VB2018 about Pegasus, including its use to target an acquaintance of the murdered Saudi journalist
Jamal Khashoggi, but made the point that most of the malware targeting civil society actually isn’t very advanced in nature. This week, we
published the video of their presentation.
Though the number of infections through
exploit kits is down from where it was a few years ago, such kits are still very active. At Virus Bulletin we actively track them, and measure the ability of web security solutions to block them. Though the block rates of tested products are generally good, a
report published last month by Virus Bulletin emphasises the point that such blocking isn't trivial: several products missed early instances of the new
Fallout exploit kit.
The SamSam indictment wasn’t the only FBI success story last week. The Bureau also announced that industry cooperation has led to the takedown of an ad fraud campaign dubbed ‘3ve’ (pronounced ‘Eve’), and an indictment against eight defendants has been unsealed.
Ad fraud campaigns tend to be very big, given the small amount of money an individual bot can generate, but 3ve was large even by those standards. Interestingly, it used two separate botnets:
Miuref (a.k.a. Boaxxe) and
Kovter. Google and White Ops published a detailed white paper (
pdf) on the operation, but many more companies and organisations were involved in the takedown.
ESET and
Symantec also published shorter analyses of 3ve and its takedown.
A different, and likely smaller, ad fraud campaign was
analysed by Dr.Web recently, which found a fake
DynDNS program downloading an ad-clicker trojan.
The ‘
Backswap’ banking trojan also uses rogue versions of legitimate apps, such as FileZilla or Notepad++, to infect users. Check Point’s Itay Cohen has written a
technical analysis of the malware and how it has evolved over time, which if anything serves as a reminder that banking malware, though in decline, is far from dead.
Cisco Talos researchers Paul Rascagnères and Warren Mercer,
speakers at the most recent Virus Bulletin Conference, have
looked at a new espionage campaign targeting high-profile entities in Lebanon and the United Arab Emirates. The campaign was dubbed ‘
DNSpionage’ and used DNS tunnelling (as well as HTTP) for C&C communication; it also involved short-lasting DNS hijacks, during which brief window Let’s Encrypt certificates for the targeted domains were registered.
Another threat group targeting the Middle East is
MuddyWater. Trend Micro researcher (and also past VB
conference speaker) Jaromir Horejsi has
discovered a new PowerShell-based backdoor, found in Turkey, that shares TTPs with known MuddyWater activity and that uses files dropped to a cloud provider for C&C communication.
The
Bladabindi remote access trojan (RAT), also known as
NJRat, has been active for at least half a decade, often in more targeted attacks; in 2015 it was the subject of a
paper published by Virus Bulletin. Trend Micro researcher Carl Maverick R. Pascual
describes how he found a new iteration of the RAT as an AutoIT-compiled worm that likely spreads via malicious USB drives.
Also from Trend Micro researchers is a new
paper on the
XLoader (a.k.a. Roaming Mantis) and
FakeSpy Android malware families. The paper notes that the two families share no fewer than 126 domain names, which leads the researchers to believe that the families were created by the same group, or at least by groups that share infrastructure. They also note code similarities between FakeSpy and malware written by the
Yanbian Gang, which has been used to steal money from South Korean banking users.
Researchers from Palo Alto’s Unit42 team have
analysed ‘
CARROTBAT’, a new piece of malware that has been used in targeted attacks in South-East Asia and that has overlap with no fewer than three other malware families:
SYSCON, KONNI and OceanSalt.
According to a
blog post by F-Secure researcher Sami Ruohonen,
French industry has been the victim of a targeted
phishing campaign. The blog post looks at the evolution of the campaign and the various redirects used to deliver the payload, including some hosted on Twitter’s own t.co domain.
Another campaign targeting industry has been analysed by Forcepoint researcher Robert Neumann, who
looked at malware targeting (and running inside)
AutoCAD.
The
civil war in Yemen has led to some terrible suffering for the local population. This being 2018, there is also a digital component to the ongoing war, which is the subject of a long and
detailed analysis from Recorded Future’s Insikt Group.
A Kaspersky
blog post on the state of malware in 2018 has confirmed the prevalence of
cryptocurrency miners. Indeed, they have been targeting just about any operating system, a fact which was corroborated by Check Point researchers, who
analysed the
KingMiner campaign targeting Windows Server.
‘
Snakemackerel’ may sound like a new malware group, but it is yet another name for the group variously known as
Fancy Bear, APT28, Sofacy or Sednit. iDefense’s Michael Yip has written a
paper on how the group is using
Brexit as a lure to deliver its Zebrocy first-stage malware.
Last month, F-Secure
found that users of the
Exodus cryptocurrency wallet for macOS were being targeted with malware containing a keylogger. Last week, SentinelOne’s Philip Stokes published a
detailed analysis of this malware.
The dangers of UPnP have been widely reported. Akamai has
analysed the
Eternal Silence malware that has compromised more than 45,000 routers with a vulnerable UPnP implementation - the company believes the malware is trying to use the
Eternalblue and Eternalred exploits against SMB to infect machines on the local network behind the router.
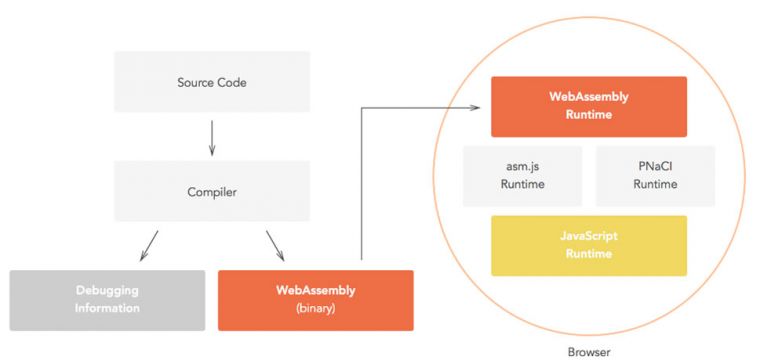
Virus Bulletin recently published a
VB2018 paper on
WebAssembly and how it could be abused by malware authors. A short, technical blog post by researcher Frank Denis
looks at how the language is safer than C, but not yet a silver bullet.
NAS boxes aren’t the first things one thinks of when it comes to malware infections, but they have been targeted in the past. On the SANS ISC blog Xavier Mertens
looks at an obfuscated bash script targeting
Qnap NAS devices.
More obfuscation techniques have featured recently in: a blog post by SpiderLabs’ Rodel Mendrez, who
analysed a
Thanksgiving spam campaign; Symantec researcher Siddhesh Chandrayan’s
analysis of how code obfuscation is used to prevent detection of
tech support scammers’ websites; and another
analysis from Xavier Mertens of a
fake Flash Player update for macOS.
Confiant has
found that
malvertising on iOS has served millions of users with gift card scams and adult content.
FireEye’s Vikram Hedge recently
looked at how
machine learning could improve the detection of malicious command lines.
G Data researchers have
shared how open-source
graph databases help them in their malware analysis.
Zoom is a widely used platform for conference calls. Tenable recently
found a vulnerability in its desktop application that could lead to control of a presenter’s desktop being hijacked. The vulnerability has since been patched.
Imperva has
looked at benign and malicious uses of the
headless version of the Chrome browser.
Morphisec has published a
detailed analysis of a malicious spam campaign that, in a number of stages, downloaded the increasingly prevalent
FlawedAmmyy remote access trojan.
And some shorter analyses looking at various kinds of spam campaigns, most of which delivered malware, have also been posted around the web:
Nanocore,
Lokibot,
Troldesh,
Dridex (via the Ursnif downloader),
Emotet,
Gootkit and
Remcos RAT, while Agari
looked at a charity scam using the recent
wildfires in California as a lure.
Finally, as alluded to in last week’s newsletter, we have finalised the Partnership Pack for
VB2019, the
29th Virus Bulletin Conference, which is to take place in London, 2-4 October 2019. If your company is interested in becoming a partner of the main event for threat intelligence researchers, or would like to be involved in some other way, please contact Allison Sketchley (
[email protected]).
© 2018 Virus Bulletin Limited
The Pentagon, Abingdon Science Park, Abingdon, Oxon, OX14 3YP, UK