One of the challenges I face when writing this newsletter is finding the links between threats and threat actors ─ links that aren’t always mentioned in the research and that may not be obvious due to different researchers giving different names to the same entities.
I was thus pleased to see a clear note in the introduction to an
ESET report on Winnti ─ linked in this newsletter ─ that clearly explains the difference between the Winnti malware and the Winnti Group behind it, while also noting that there may actually be multiple groups behind this name.
Security companies tend to see good research as a PR and marketing tool. While it is only fair for companies to boast about the quality of their research output, they should note that many of the readers of such reports will be fellow researchers and journalists, for whom links to other research and openness about the many unknowns are vital.
This is a separate issue from attribution being difficult, a view that was highlighted by the news that the NSA and GCHQ
accuse Russia’s Turla group of having hijacked the infrastructure of Iran’s OilRig actor ─ something previously
implied by Symantec. Those interested in this kind of ‘fourth party collection’ could do worse than read the
VB2017 paper on this subject written by Juan Andrés Guerrero-Saade and Costin Raiu, or watch the corresponding
video of their presentation.
Martijn Grooten
Editor, Virus Bulletin
For the privacy conscious among you: we do not track clicks on the links contained in this newsletter to individual subscribers, but should you feel more comfortable, we believe that any of the links mentioned here can be found through search engines.
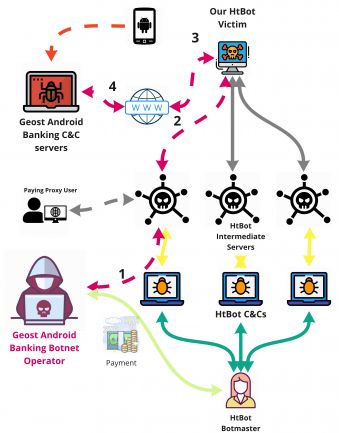
Researchers Sebastian Garcia (Czech Technical University in Prague), Maria Jose Erquiaga (National University of Cuyo) and Anna Shirokova (Avast) were looking at the HtBot malware that turned infected machines into proxies when they noticed this proxy network being used to access the command and control of another botnet. This ‘
Geost’ botnet turned out to be a very large Android banking botnet with many victims in Russia. The researchers wrote a paper on Geost that Sebastian and Anna presented at VB2019 in London. We have now published
their paper on our website and also uploaded the
video of their presentation to YouTube.
Reason Cybersecurity was one of the partners of this year’s VB2019 conference and, when invited to write a guest post for our blog, Reason researchers came up with a
detailed analysis of malware that is responsible for sending a
sextortion spam campaign, while also mining for the Monero cryptocurrency on infected hosts. The same malware, dubbed ‘
Save Yourself’ after the From: addresses, was also
analysed by Check Point researchers.
The Dukes is a cyber-espionage group, better known as APT29 or
Cozy Bear, and believed to be behind the 2016 DNC hack. Since then, only a
2018 phishing campaign has been attributed to the group. However, a
new paper by ESET reports that The Dukes has never ceased its activities. The paper details ‘Operation Ghost’, which dates back to 2013 and which has been focusing on government targets, including European Ministries of Foreign Affairs. The paper details the continued use of the MiniDuke backdoor,
first analysed by Kaspersky and CrySyS in 2013, as well as four previously unknown -Duke malware families. Interestingly, malware linked to the Turla and Fancy Bear APT group, also believed to be Russian, was found on some of the affected computers. This confirms previous reports of little cooperation among Russian government actors.
Emsisoft’s
ransomware statistics, which are based on submissions to its ID ransomware service, show a bias within the security community towards malware hitting honeypots in some way, as opposed to malware that is bundled with software cracks and keygens. Emsisoft says that more than half the submissions refer to the not widely reported
STOP (or DJVU) ransomware, distributed via torrents. For many victims of this ransomware there is good news though: Emsisoft has released a
decryption tool for 148 out of 160 known variants.
In August, FireEye published a
detailed report on
APT41, a Chinese threat actor that at least partly overlaps with Winnti. In a new
blog post, FireEye researcher Tobias Krueger analyses
LOWKEY, a backdoor used by this group in some targeted attacks, and variants of the DEADEYE malware delivering it.
Those interested in APT41/
Winnti, and in particular the supply-chain attacks the Winnti group is usually associated with, should read a
whitepaper ESET researchers published last week. In it, they analyse malware used by the group ─ in particular the
PortReuse backdoor and the
VMProtect packer ─ that had not been fully analysed in public before, while also linking the various supply-chain events this group has been associated with.
TA505 is one of the most prolific cybercrime actors that, in recent years, has been targeting financial institutions directly. In a
new analysis, Proofpoint looks at a recent email campaign of the group in which a new downloader, dubbed ‘Get2’, is used to push the also new
SDBbot RAT. The latter RAT was analysed in a recent threat report by AhnLab (
pdf), which found it being used as a secondary payload to the FlawedAmmyy RAT in campaigns targeting South Korea.
Fallout is one of several active exploit kits and one that we actively track in our
web security lab. Bitdefender has published a
paper containing a detailed technical analysis of Fallout that also looks at the
Raccoon information stealer, one of several payloads pushed by Fallout.
In tech circles, ‘the blockchain’ is often mockingly referred to as a solution looking for a problem, but some malware authors appear to have found such a problem: Check Point researchers Kobi Eisenkraft and Arie Olshtein
describe how the operators of the
Redaman banking trojan use the Bitcoin blockchain to store the IP addresses from which the
Pony malware was downloaded onto infected systems.
TA407, also known as
Cobalt Dickens or Silent Librarian, is a threat actor operating out of Iran whose main targets are academic libraries in the United States. The subject of reports by both
Proofpoint and
Secureworks last month, the group is now covered in a
new profile by Proofpoint which has more technical details on the credible phishing campaigns sent out by the actor.
The
recently discovered checkm8 iOS exploit has led to an increased interest in iPhone jailbreaks, which has, perhaps unsurprisingly, led to scams. Cisco Talos researchers Warren Mercer and Paul Rascagnères, members of the team that won the most recent
Péter Szőr Award,
write about a fake download that claims to be the jailbreak but which forces users to install a malicious profile which is then used for
click-fraud.
The increased commoditization of cybercrime has led to markets that allow malware to be used in the wild shortly after it is first sold. Such is the case of the
Blackremote RAT, a new RAT developed and sold by an 18-year-old Swedish man, that was
analysed by Palo Alto Networks’ Unit 42 team.
A Cisco Talos
report from last year called the ‘
Rocke’ actor ‘the champion of Monero miners’. The China-based actor is still active and continues to evolve, according to an
analysis by Anomali, which noted the switch to DNS TXT records to locate the C&C server, as well as new exploits being added.
ESET researcher Anton Cherepanov
found a trojanised version of the
Tor Browser that had the HTTPS Everywhere plug-in modified to inject some JavaScript code into the browser session. The purpose of this was to steal bitcoins ─ an activity in which the actors behind the malware appear to have been successful: Anton noted that at least $40k worth of Bitcoin was stolen this way.
In June, Symantec
described how the Turla APT group encoded malicious code inside
.wav files. Now, Cylance
reports more examples of this kind of steganography, some but not all of which use .wav files that actually play music, and that deliver
Monero miners or, as in the Turla case, a Metasploit payload.
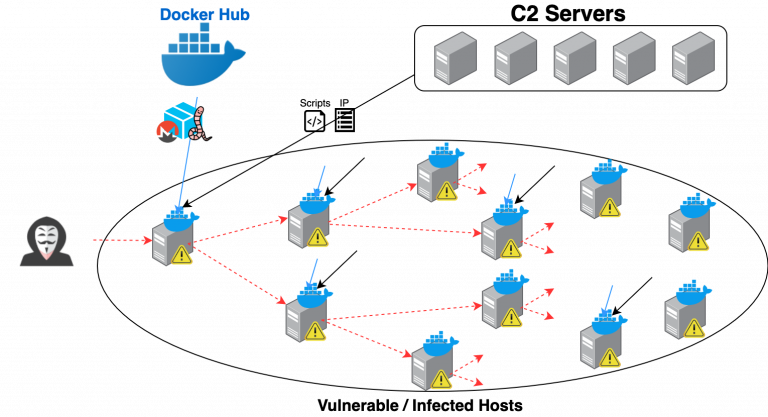
The increased value of cryptocurrencies has led to a resurgence of malware mining such currencies on infected devices. Palo Alto Networks’ Jay Chen has
analysed ‘
Graboid’, the first cryptomining worm that downloads copies of itself from Docker Hub to infect unsecured Docker engines.
Trend Micro researcher Song Wang has
analysed a fake photo beautification Android app that has the ability to read
SMS verification codes and turn on WAP billing ─ a sure-fire way to steal money from those installing the app.
A
report by Advanced Intelligence looks at the increased commoditization of
ransomware operations, with access being sold to compromised company networks to install ransomware.
Malicious actors have started to focus on the 2020 US Presidential elections. Digital Shadows
looks at typosquatted domains linked to the various 2020 contenders.
Kaspersky recently
wrote about ‘Operation AppleJeus’, in which the
Lazarus Group targeted cryptocurrency exchanges using malware for both Windows and macOS. The former variant, in particular the x86 version, has now been
taken apart by Vitali Kremez on his own blog.
Cofense has
analysed a
phishing campaign targeting
Stripe, where a simple HTML trick was used to hide the link’s real destination from a suspicious user.
Vulnerable plug-ins are a common way for
WordPress sites to get infected, but sometimes, as a Sucuri
blog post explains, malicious plug-ins are used on compromised sites to facilitate malicious behaviour.
The SANS Internet Storm Center blog features an
analysis by Xavier Mertens of a huge
VBS file sent in a malicious email campaign through a link and packed inside a zip.
On his blog, Brad Duncan
looked at a malicious spam campaign that served the
Troldesh (a.k.a. Shade) ransomware to Russian users via a link in a PDF attachment. We spotted several of these emails in our
email security test lab too, and noted several products failing to block the emails.
The
Ordinypt malware is a strong argument for the case that paying the ransom doesn’t guarantee you will get your files back: the malware pretends to be ransomware and actually demands a fee for decryption, but in reality it is a wiper with no possibility for file recovery. As the malware has recently seen a resurgence, still mostly targeting German companies, G DATA researchers
analysed it.
Finally, in recent years both
Kaspersky and
Trend Micro have written about the
Cutlet Maker ATM malware that is installed via a USB drive and then ejects all the cash inside the ATM through a ‘jackpotting’ attack. The banking sector doesn’t often report on such incidents, but a joint investigation from
Motherboard and, in German, the
Bavarian public broadcaster, suggests that some 1.5m euros have been stolen using this malware.
© 2019 Virus Bulletin Limited
The Pentagon, Abingdon Science Park, Abingdon, Oxon, OX14 3YP, UK